Dr. Michael Thomas is the original author of Geography 489 " Cyber-Geography in Geospatial Intelligence", and is also one of the instructors for Geography 882. He has worked as an analyst for HQEUCOM in Stuttgart, Germany, in the Cyberspace Division, as a Professor of Cyberwarfare Studies at the AIr War College and USAF Cyber College at Maxwell AFB and is currently the Deputy Director of the National Cyber Range Complex (NCRC) - Charleston Node. He is very interested in how geographic information science and technology (GIS&T) can be applied to the emerging field of Cyberspace both within and outside the government. There are two dimensions to Cyberattacks – collecting of intelligence from nations that are of interest to us, and realizing that others are constantly collecting on us.
Information is the only asset that is stolen by replication. As such, securing it is problematic because for it to be of any use it also needs to be available for access. In the wake of the September 11, 2001 attacks, the US government began instituting information protection policies aimed at increasing homeland security. The aim of these policies was to minimize the targets of opportunity that could be exploited by potential attackers using publicly available information they might obtain from authoritative public (federal, state and local) sources in planning attacks against the US homeland.
One of the outcomes of these policies is the “National Cybersecurity Strategy” that was released in March 2023. The DoD has stated that “The Department and the nation have vulnerabilities in cyberspace. Our reliance on cyberspace stands in stark contrast to the inadequacy of our cybersecurity – the security of the technologies that we use each day.” DoD strategy flows from both the National Cybersecurity Strategy and the National Defense Strategy.
There are thousands of networks, incalculable data assets freely in the open, and adversaries – individuals, groups, and nation-states, that can and will use our own information sources against us. It raises the question – how much information should a free society place in the open?
Required Readings
- "Mapping the Risks" is a Rand study complied in 2004. It attempts to evaluate the risks and rewards of having easily accessible Geospatial data available online for use by anyone. Although federal agencies produce and publicly disseminate geospatial information for a wide range of beneficial purposes, there also exists the risk that some types of geospatial information could be and has been exploited by terrorists. This is the challenge the federal agencies face in deciding which types of geospatial information should be publicly accessible, as well as whether and how to restrict new sensitive information as it becomes available.
The full study is available from The Rand Corporation Website.
NOTE: For this assignment, you need only read the Executive Summary.
- The Office of the President released the "National Cybersecurity Strategy" in March 2023. It has been an ever evolving document, the latest being the 2023 "National Cybersecurity Strategy."
Between 2004 and 2023, Cyberspace evolved into a mature operating domain. For many reasons, many of them political or driven by DOD component infighting, no final concrete policy existed before this and the debate to establish a separate CYBERCOM took years to finalize between the sister services within the DoD, with a final definition of cyberspace finally being imposed on the DoD by Gordon England in May 2008.
Readings can be accessed from the Lesson 10 Checklist.
You will compare and contrast these two publications that lay out some of the basics of Geo-based Cyberspace analysis and cyber map production.
As you read, do some critical thinking and ask yourself:
- What aspects of the application of GIS&T in the military and the intelligence community are really applications of geospatial intelligence?
- Given what you know of the application of geospatial intelligence to US national security activities, compare and contrast how the DoD intelligence community leverages GIS&T and the intelligence process.
- Given that GIS&T includes at least the four subfields of cartography, remote sensing, GIS, and GPS, consider the central role that mapping seems to play in cyber analysis. How might the DoD and the intelligence community better leverage the other components of GIS&T and geospatial intelligence?
Required Viewing
Video: The Cyber War Threat Has Been Grossly Exaggerated. (1:38:00) (Transcript)

The debate still continues. After listening, offer a perspective of whether the debate affected your view.
- Which way did you vote at the beginning?
- Which way did you vote at the end?
- Offer your insights as to whether the debate is real or exaggerated.
Information Technology Infrastructure
Information technology infrastructure has changed in the last 10 years. Currently, an integration of geolocating technologies with communications infrastructures has made possible dynamic changes in Northern Africa and parts of the Middle East.
Let us examine a few facts concerning the integration of technologies in Africa over the last decade.

Low-cost, abundant, easily distributed information lowers transaction costs, which affects the nature of institutions and organizations. When internet connectivity was mostly carried on satellites it (and the transaction costs) was high. As these cables come online, the transactions costs are going to come down. Infrastructure increases in Africa will eventually lead to increases in information flow and associated increases in relational aspects between distant points. What could formerly be characterized as "Terra Incognita" is changing with increases in infrastructure.
Would the "Arab Spring" have been possible before 2009? The lack of infrastructure makes it doubtful. Once all the cables are in place, Africa's total bandwidth will increase from 6 terabytes/second (tbps) to well over 40tbps. Currently, there are over half a billion Africans connected to the global system through cell phones and the Internet, and this number is going to dramatically increase.
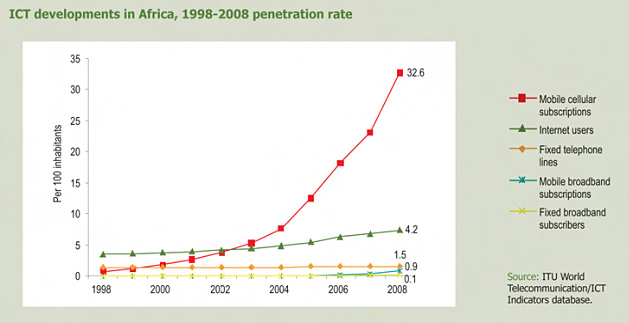
The graph above shows the continent-wide penetration rate of different Information-Communication technologies (ICTs). Notable here is the huge increase in wireless penetration - almost 33% continent-wide that does not require as much infrastructure as traditional landlines. This continent-wide picture does not paint a fully accurate picture. While the overall number is correct, the penetration rates in North Africa show a different story when reviewed separately. Too much variation is concealed in the overall continental rate but becomes apparent when examined more regionally. In the Mahgreb, the rates were almost twice as much as the continental average and increased steadily to over 100% in some places, meaning that some subscribers actually had more than 1 phone by 2010.
The former Director of National Intelligence (DNI), General James Clapper, hinted at the IC's interests in some of the aspects of intelligence collection in an interview in the December 2011 issue of Geospatial Intelligence Review,
"I see all kinds of benefits (from combining collection and analysis). There are a lot of examples that I can't cite because they are classified. But I will say that I think we will be better able to address an Arab Spring, for example, and better able to anticipate it and respond to it."
The richness of available open source data, generated either by social media or other sources, is too complex to accumulate and analyze using current approaches. Currently, analysts often use multiple sources of information in order to create actionable intelligence for a mission. The datasets are large in volume and are likely stored in multiple databases and multiple locations. This requires tailored queries into the systems to be prespecified, filtering significant amounts of data before an analyst has an opportunity to decide if it is important. This query-retrieve paradigm effectively removes the possibility of the "lucky find," because the analyst has to already know what they want to query. Looking forward, the datasets are becoming more connected and the transaction costs are decreasing. The volume of pseudo-humint available from social media is one result of the increase in this connectivity infrastructure, and the impacts are both unpredictable and unforeseen. At a minimum, it raises the following questions for our consideration:
- The tacit-explicit knowledge transformation underway is potentially making disconnected areas such as Africa less a "Terra-Incognita" than ever before. What will this mean in terms of the geo-strategic framework?
- How seriously is the IC reviewing the potentials of Web 2.0 enabled sources geospatially enabled with "Volunteer Geographic Information?"
- How might peer and near peer opponents make use of the models?
Emerging technologies also pose unique challenges and threats. ChatGPT, when queried about the threats in cyber to GeoInt replied:
"The dangers of cyberspace in the GeoInt (Geospatial Intelligence) environment are multifaceted and significant. They can be categorized into several key areas:
-
Cyber Espionage and Data Theft: In a GeoInt environment, where sensitive geospatial data is used, cyber espionage is a major threat. Unauthorized access to this data can lead to the theft of classified information, compromising national security and intelligence operations.
-
Cyberattacks on Critical Infrastructure: GeoInt often involves infrastructure critical to national security, like satellite communications, GPS systems, and other space-based assets. Cyberattacks on these systems can disrupt essential services, leading to significant strategic disadvantages.
-
Manipulation of Geospatial Data: The integrity of geospatial data is crucial. If this data is manipulated or altered, it can lead to incorrect intelligence assessments, affecting decision-making in critical situations such as military operations or disaster response.
-
Information Warfare: In the realm of GeoInt, information warfare, including the spread of misinformation and propaganda, can be facilitated through cyberspace. This can undermine trust in institutions and disrupt geopolitical stability.
-
Supply Chain Attacks: GeoInt systems often rely on a complex supply chain that includes software and hardware components from various sources. Cyberattacks targeting these supply chains can compromise the integrity of geospatial intelligence systems.
-
Insider Threats: The risk posed by insiders, such as employees or contractors with access to GeoInt systems, is significant. They might intentionally or unintentionally cause harm by leaking sensitive information or introducing vulnerabilities into the system.
-
Lack of Standardized Security Protocols: In the GeoInt environment, the lack of standardized cybersecurity protocols across different nations and organizations can create vulnerabilities. Disparate systems and practices can lead to gaps in security defenses.
-
Emerging Technologies: The rapid evolution of technology, including AI and quantum computing, presents new challenges in cybersecurity. These technologies can be used to create more sophisticated cyberattacks that are harder to detect and defend against.
-
Legal and Ethical Concerns: Navigating the legal and ethical aspects of cyber operations in GeoInt is complex, especially when it comes to cross-border data sharing and surveillance activities.
-
Resource Constraints: Finally, the challenge of allocating adequate resources (like skilled personnel and funding) to cybersecurity in the GeoInt sector cannot be overlooked. This includes the need for continuous training and updating of systems to counter evolving cyber threats.
Given these threats, it's crucial for organizations and nations involved in GeoInt to invest in robust cybersecurity measures, conduct regular risk assessments, and foster international cooperation to enhance collective cyber defense capabilities."
Reference:
CHAT GPT, response to “threats in cyber to GeoInt,” CHAPT GPT, Dec. 3, 2023.